The topic of certificates seems to be haunting me at the moment.
Anyway, I want to briefly show here how easy it is nowadays to replace the SSL certificate of the vCenter with an Enterprise CA-signed one.
If you look at the KB article from VMware (Replacing a vSphere 6.x /7.x Machine SSL certificate with a Custom Certificate Authority Signed Certificate), the “certificate-manager” is still quoted here on the command line.
Create CSR in vSphere Client
But it is also very easy via the vSphere Client. In my case, there are a couple of VxRail clusters connected to this vCenter, here you also have to do something in the VxRail Manager (in this case still via CLI), but it’s also easy, see below.
To the Demo!
Login to vCenter and go to Administration >> Certificate Management, then __MACHINE_CERT >> Actions >> Generate Certificate Signing Request:
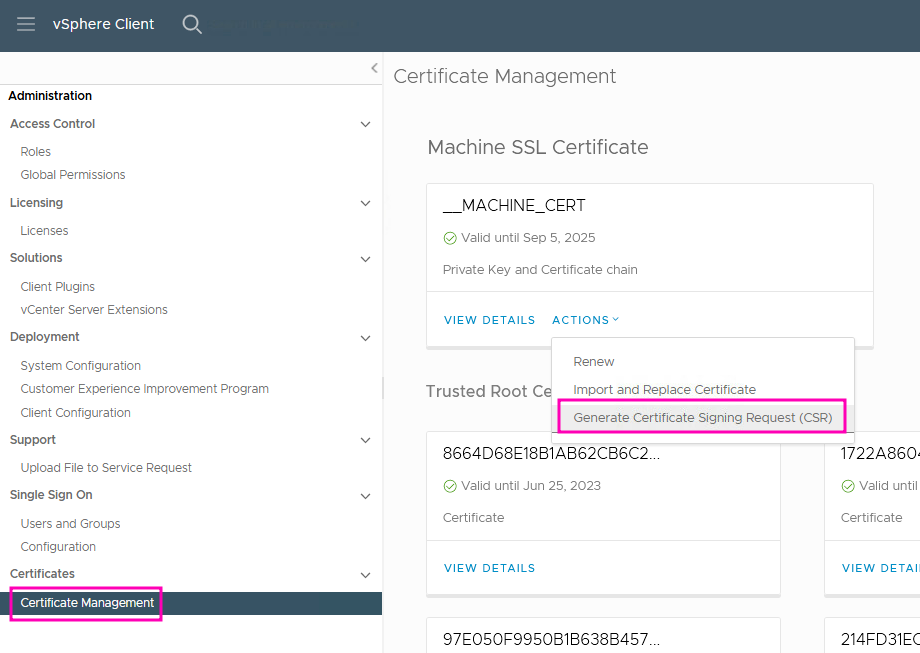
Put in all info for the Signing Request:
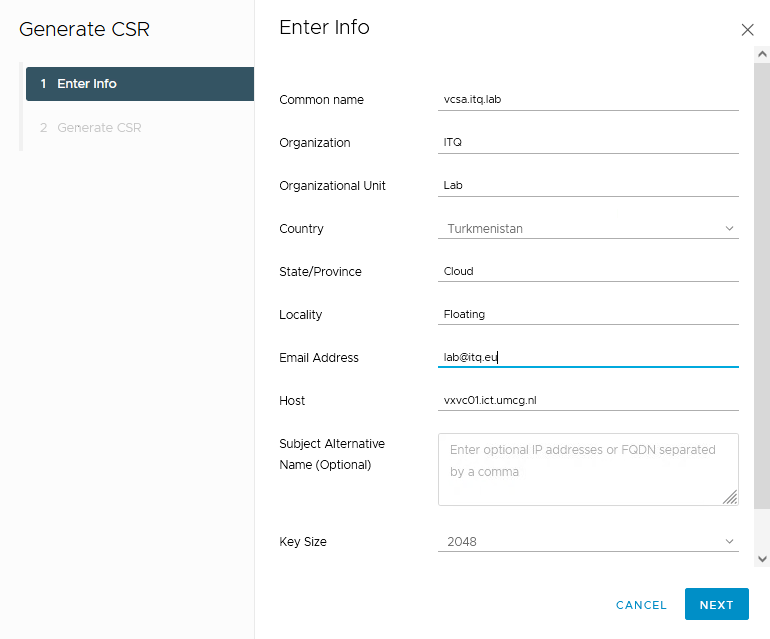
…and either copy or download the CSR:
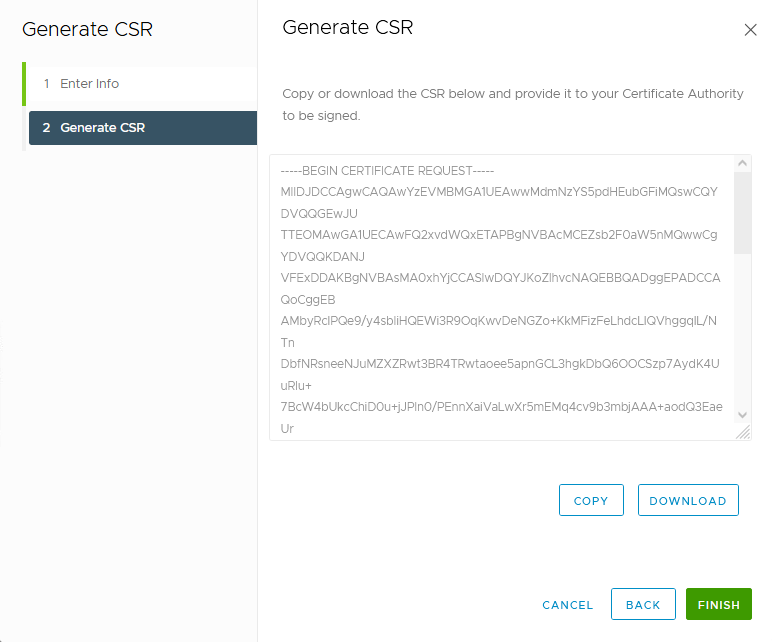
Well, that was easy!
The something.csr file is now required by the certificate admin(s), or, if you do this with the Windows CA, there may also be a self-service portal, but this is not the topic here (but it could work as in this blog post).
The CSR has been submitted, what’s next?
After creating a certificate from the CSR, we should now have a CER file and a certificate chain file, both available from our CA.
Back to vSphere Client, this time Administration >> Certificate Management, then __MACHINE_CERT >> Actions >> Import and Replace Certificate:
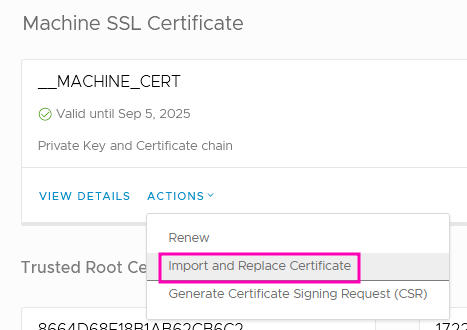
Then “Replace with external CA certificate where CSR is generated from vCenter Server”:
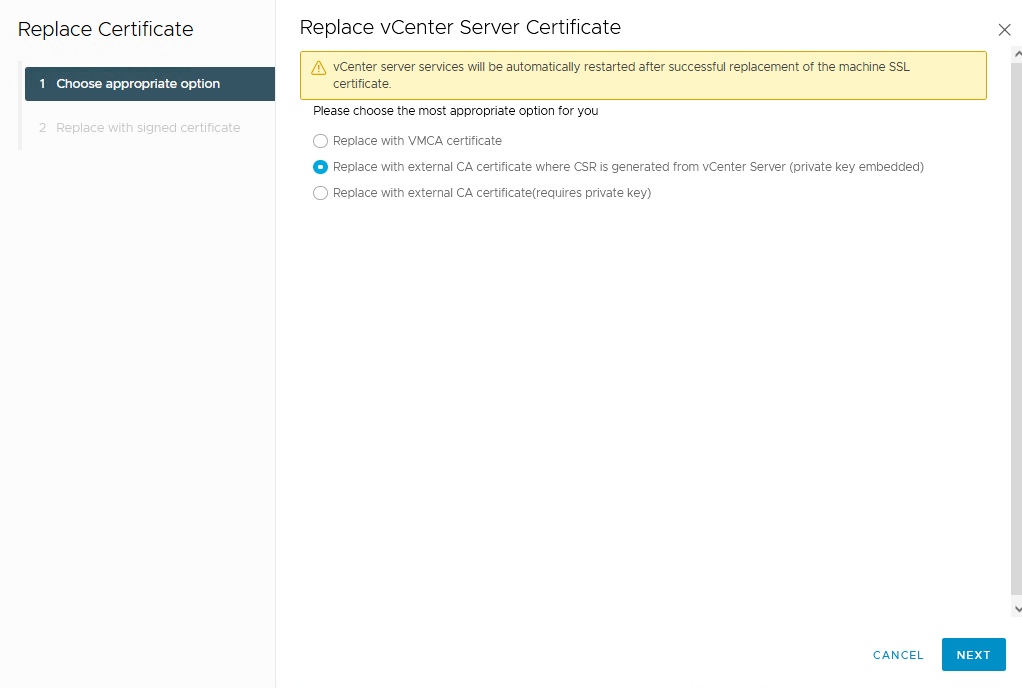
Hadn’t mentioned it yet: the advantage of a CSR from the vCenter is that the private key is already “embedded”. With a CSR that was not created on the vCenter, it is missing. You would then have to get it additionally and select option 3.
Anyway, with option 2, it then goes on like this:
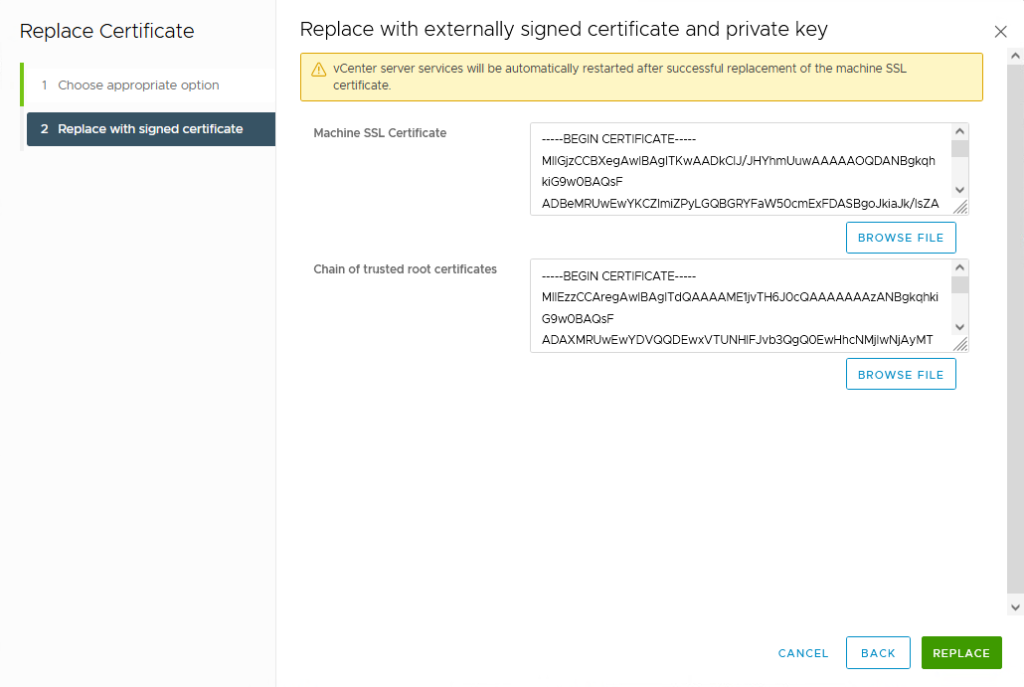
Select a new CER file from the CA (Machine SSL Certificate) and select a chain certificate file from the CA (Chain of trusted root certificates) and click Replace.
Attention: now the vCenter services restart! This will not take long, but should probably not be done in productive environments without prior consultation.
If you are impatient (F5!!! F5!!! F5!!!) and can already log in again, the certificate overview may look a bit strange and also spit out a few errors. Relax and give it a few minutes!
And that’s it, the vCenter now has a “Trusted Certificate” from its own CA and the browser is no longer annoying with security warnings.
The VxRail Manager also wants to get back on!
If there are applications that talk to the vCenter ( this can happen), such as vRealize Log Insight, vRealize Automation, vRealize Operations, Skyline Advisor, VxRail Manager,…. then they do not yet know about their luck and should be adjusted (by re-authentication or similar).
IIn my case, there are a few VxRail Managers here that now have no “trust” with the vCenter, but this can be fixed with a Python script (available from Dell in the support article VxRail: How to manually import vCenter SSL certificate on VxRail Manager). The script is updated from time to time, so always check back first!
So:
- Load the script onto the VxRail Manager (e.g. via WinSCP).
- log in as “mystic” via SSH
- “su” to user “root”
- execute script:
python cert_util.py
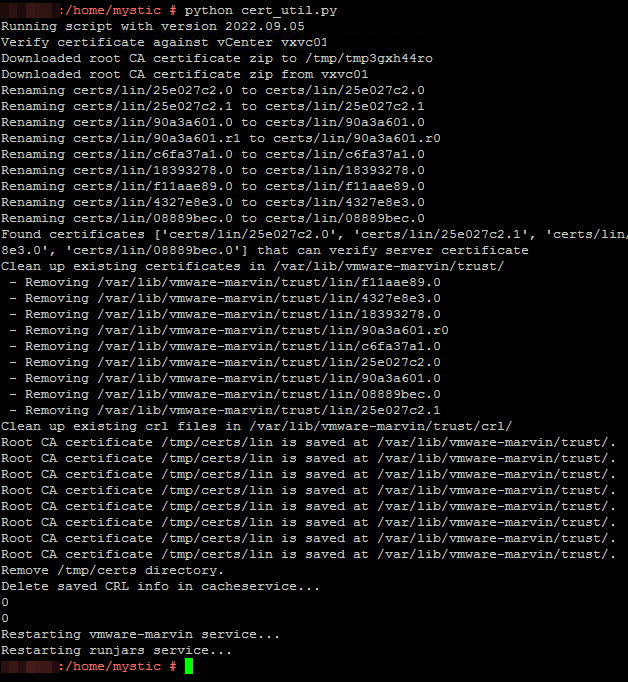
As you can see, the script loads the new CA certificate from vCenter, replaces the existing ones with it and then restarts a few services. Done.
Easy!
In my experience, the use of self-signed certificates is still a rarity, but the effort is small. The CSR is generated in no time and the certificates are quickly exchanged in the vSphere Client.
